Multi-VLAN Segmentation with Trunking and ROAS
Overview
Designed a multi-VLAN network using two switches and a router, configured trunk ports and VLANs across switches, and implemented Router on a Stick (ROAS) to enable inter-VLAN communication across departments.
| Skills Demonstrated |
|---|
| Creating and assigning VLANs for department-based segmentation |
| Calculating and applying subnetting for scalable IP allocation |
| Creating and configuring trunk ports between switches and to the router for VLAN propagation |
| Naming and managing VLANs using best practices |
| Simulating a multi-department structure: Sales (VLAN10), HR (VLAN20), Engineering (VLAN30) |
| Implementing Router on a Stick (ROAS) with subinterfaces using encapsulation dot1q |
| Setting native VLAN to VLAN1001 for trunk security |
| Verifying trunk status, VLAN propagation, and ROAS functionality via ping tests |
| Demonstrating inter-VLAN connectivity with ping replies across VLANs on different switches |
| Tools Used |
|---|
| Cisco Packet Tracer |
| Switch CLI |
| Router CLI |
| Straight Through & Crossover Cables |
| PC Static IP Configuration Panel |
| Command Line Utilities (ping, show vlan brief, show interface trunk, show ip interface brief) |
1. Network Topology
I separated 8 PCs into 3 VLANs per department with VLAN20 being extended across a switch:
- VLAN10: Sales
- VLAN20: HR
- VLAN30: Engineering

For each VLAN in this example, I went with a /26 subnet which would give me 62 usable hosts to allot for each department to add new PCs to the subnet in the future:
| VLAN | Department | Network Address | Usable Range | Broadcast Address | Gateway |
|---|---|---|---|---|---|
| VLAN10 | Sales | 10.0.0.0 | 10.0.0.1 - 10.0.0.62 | 10.0.0.63 | 10.0.0.62 |
| VLAN20 | HR | 10.0.0.64 | 10.0.0.65 - 10.0.0.126 | 10.0.0.127 | 10.0.0.126 |
| VLAN30 | Engineering | 10.0.0.128 | 10.0.0.129 - 10.0.0.190 | 10.0.0.191 | 10.0.0.190 |
Since they are different devices, I then connected straight through cables from each PC to their respective switch:
- PC1 F0/0 → SW1 F0/1 (VLAN10)
- PC2 F0/0 → SW1 F1/1 (VLAN10)
- PC3 F0/0 → SW1 F2/1 (VLAN20)
- PC4 F0/0 → SW1 F3/1 (VLAN20)
- PC5 F0/0 → SW2 F0/1 (VLAN30)
- PC6 F0/0 → SW2 F1/1 (VLAN30)
- PC7 F0/0 → SW2 F2/1 (VLAN20)
- PC8 F0/0 → SW2 F3/1 (VLAN20)

For this lab, since I will be performing ROAS (Router on a Stick) and I am extending VLAN20 across a switch, I connect a crossover cable from SW2 to SW1 and a straight-through cable from SW1 to R1, and they will become trunk ports.
- SW1 F4/1 → SW2 F4/1 (Trunk - VLAN20, VLAN30)
- SW1 G7/1 - R1 G0/0 (Trunk - VLAN10, VLAN20, VLAN30)

2. PC Configuration
Then I go into each PC's config settings and set the appropriate IP address and subnet mask based on the /26 subnet:

I then go to each PC and set the default gateway in the config settings to the last usable address of each subnet range. This is necessary for the inter-vlan routing when I set the IP addresses on the router later:

The final IP configurations for the PCs:
| PC | IP Address | Subnet Mask | Gateway |
|---|---|---|---|
| PC1 | 10.0.0.1 | 255.255.255.192 | 10.0.0.62 |
| PC2 | 10.0.0.2 | 255.255.255.192 | 10.0.0.62 |
| PC3 | 10.0.0.65 | 255.255.255.192 | 10.0.0.126 |
| PC4 | 10.0.0.66 | 255.255.255.192 | 10.0.0.126 |
| PC5 | 10.0.0.129 | 255.255.255.192 | 10.0.0.190 |
| PC6 | 10.0.0.130 | 255.255.255.192 | 10.0.0.190 |
| PC7 | 10.0.0.67 | 255.255.255.192 | 10.0.0.126 |
| PC8 | 10.0.0.68 | 255.255.255.192 | 10.0.0.126 |
After setting up the IP address and subnet mask for each PC, I do a quick ping check on PC1.
From PC1, I first ping 10.0.0.2 (PC2) to confirm that I get replies, and then ping 10.0.0.65 (PC3) which is in a different subnet. I do this to confirm that it can't yet reach PC3 since it's in a different subnet. They will be able to ping each other later once I set up inter-vlan routing.

3. Switch Configuration - Access Ports
Now, I begin the process to add each PC to their appropriate VLAN by setting the access ports on the switch to VLAN. Before that, I set up some initial settings on the switch.
First, I enable an MD5 secret password on the switches for security best practices and save it to startup configuration:
Switch> enable
Switch# conf t
Switch(config)# enable secret [password]
Switch(config)# exit
Switch# write
Then I change the hostname from "Switch" to "SW1" and "SW2" just to make it easier to know which switch is which:
SW1
Switch> enable
Switch# conf t
Switch(config)# hostname SW1
SW1(config)# exit
SW1# write
SW2
Switch> enable
Switch# conf t
Switch(config)# hostname SW2
SW2(config)# exit
SW1# write
Now that I enabled the secret password and changed the hostname, it's time to configure the interfaces to join the VLANs.
First I run "show vlan brief" in the following commands to see the VLAN status of each ports. We can see that the default native VLAN1 and the other defaults of VLAN1002 - 1005 are set and that each port on both switches is currently in VLAN1:
SW1> enable
SW1# show vlan brief
| VLAN | Name | Status | Ports |
|---|---|---|---|
| 1 | default | active | Fa0/1, Fa1/1, Fa2/1, Fa3/1, Fa4/1, Fa5/1, Fa6/1, Gig7/1 |
| 1002 | fddi-default | active | |
| 1003 | token-ring-default | active | |
| 1004 | fddinet-default | active | |
| 1005 | trnet-default | active |
SW1
First I configure f0/1 and f1/1 on SW1 to VLAN10 and name VLAN10 "Sales" by running the following commands:
SW1> enable
SW1# conf t
SW1(config)# int range f0/1,f1/1
SW1(config-if-range)# switchport access vlan 10
SW1(config-if-range)# exit
SW1(config)# vlan 10
SW1(config-vlan)# name Sales
Next I configure f2/1 and f3/1 on SW1 to VLAN20 and name VLAN20 "HR" by running the following commands:
SW1> enable
SW1# conf t
SW1(config)# int range f2/1,f3/1
SW1(config-if-range)# switchport access vlan 20
SW1(config-if-range)# exit
SW1(config)# vlan 20
SW1(config-vlan)# name HR
Now when running "show vlan brief" on SW1 we can see each port is assigned to the correct VLAN and has the proper name:
| VLAN | Name | Status | Ports |
|---|---|---|---|
| 1 | default | active | Fa6/1, Gig7/1, Gig8/1 |
| 10 | Sales | active | Fa0/1, Fa1/1 |
| 20 | HR | active | Fa2/1, Fa3/1 |
| 1002 | fddi-default | active | |
| 1003 | token-ring-default | active | |
| 1004 | fddinet-default | active | |
| 1005 | trnet-default | active |
SW2
Now on SW2, first I configure f0/1 and f1/1 to VLAN30 and name VLAN30 "Engineering" by running the following commands:
SW2> enable
SW2# conf t
SW2(config)# int range f0/1,f1/1
SW2(config-if-range)# switchport access vlan 30
SW2(config-if-range)# exit
SW2(config)# vlan 30
SW2(config-vlan)# name Engineering
Next I configure f2/1 and f3/1 on SW2 to VLAN20 and name VLAN20 "HR" by running the following commands:
SW2> enable
SW2# conf t
SW2(config)# int range f2/1,f3/1
SW2(config-if-range)# switchport access vlan 20
SW2(config-if-range)# exit
SW2(config)# vlan 20
SW2(config-vlan)# name HR
Now when running "show vlan brief" on SW2 we can see each port is assigned to the correct VLAN and has the proper name:
| VLAN | Name | Status | Ports |
|---|---|---|---|
| 1 | default | active | Fa4/1, Fa5/1, Fa6/1, Fa7/1, Fa8/1, Fa9/1 |
| 20 | HR | active | Fa2/1, Fa3/1 |
| 30 | Engineering | active | Fa0/1, Fa1/1 |
| 1002 | fddi-default | active | |
| 1003 | token-ring-default | active | |
| 1004 | fddinet-default | active | |
| 1005 | trnet-default | active |
4. Switch Configuration - Trunk Ports
Next I need to set up my trunk ports from SW1 → SW2 and SW1 → R1
SW1
On SW1, I set the f4/1 interface to a trunk port and allow VLAN20 and VLAN30 since those are the VLANs being extended from SW2 and set the default native VLAN to 1001 for security purposes.
SW1> enable
SW1# conf t
SW1(config)# int f4/1
SW1(config-if)# switchport mode trunk
SW1(config-if)# switchport trunk allowed vlan 20,30
SW1(config-if)# switchport trunk native vlan 1001
# I have to allow VLAN30 since it wasn't configured on this switch yet
SW1(config)# vlan 30
Now that interface F4/1 is set as a trunk port, I also need to set interface G7/1 as a trunk port connected to R1 since I will be configuring ROAS later.
SW1> enable
SW1# conf t
SW1(config)# int g7/1
SW1(config-if)# switchport mode trunk
SW1(config-if)# switchport trunk allowed vlan 10,20,30
SW1(config-if)# switchport trunk native vlan 1001
SW2
On SW2, I set the f4/1 interface to a trunk port and allow VLAN20 and VLAN30 as well and set the default native VLAN to 1001 for security purposes.
SW2> enable
SW2# conf t
SW2(config)# int f4/1
SW2(config-if)# switchport mode trunk
SW2(config-if)# switchport trunk allowed vlan 20,30
SW2(config-if)# switchport trunk native vlan 1001
Now when running "show interface trunk" on SW1 we can see the following output:
| Port | Mode | Encapsulation | Status | Native VLAN |
|---|---|---|---|---|
| Fa4/1 | on | 802.1q | trunking | 1001 |
| Gig7/1 | on | 802.1q | trunking | 1001 |
| Port | VLANs Allowed on Trunk |
|---|---|
| Fa4/1 | 20,30 |
| Gig7/1 | 10,20,30 |
| Port | VLANs Allowed and Active in Management Domain |
|---|---|
| Fa4/1 | 20,30 |
| Gig7/1 | 10,20,30 |
| Port | VLANs in STP Forwarding State and Not Pruned |
|---|---|
| Fa4/1 | 20,30 |
| Gig7/1 | 10,20,30 |
And when we run the same command on SW2 we see a similar output, minus the G7/1 port, letting us know the trunk link is working:
| Port | Mode | Encapsulation | Status | Native VLAN |
|---|---|---|---|---|
| Fa4/1 | on | 802.1q | trunking | 1001 |
| Port | VLANs Allowed on Trunk |
|---|---|
| Fa4/1 | 20,30 |
| Port | VLANs Allowed and Active in Management Domain |
|---|---|
| Fa4/1 | 20,30 |
| Port | VLANs in STP Forwarding State and Not Pruned |
|---|---|
| Fa4/1 | 20,30 |
5. Router Configuration - ROAS
Now to configure Router on a Stick for R1 and create subinterfaces, I run the following commands:
R1> enable
R1# conf t
R1(config)# int g0/0.10
R1(config-subif)# encapsulation dot1q 10
R1(config-subif)# ip address 10.0.0.62 255.255.255.192
R1(config-subif)# int g0/0.20
R1(config-subif)# encapsulation dot1q 20
R1(config-subif)# ip address 10.0.0.126 255.255.255.192
R1(config-subif)# int g0/0.30
R1(config-subif)# encapsulation dot1q 30
R1(config-subif)# ip address 10.0.0.190 255.255.255.192
Now when I run the "show ip interface brief" command on R1 we can see the following subinterfaces added with the correct IP addresses:
| Interface | IP Address | OK? | Method | Status | Protocol |
|---|---|---|---|---|---|
| GigabitEthernet0/0 | unassigned | YES | manual | up | up |
| GigabitEthernet0/0.10 | 10.0.0.62 | YES | manual | up | up |
| GigabitEthernet0/0.20 | 10.0.0.126 | YES | manual | up | up |
| GigabitEthernet0/0.30 | 10.0.0.190 | YES | manual | up | up |
| GigabitEthernet0/1 | unassigned | YES | manual | up | down |
| GigabitEthernet0/2 | unassigned | YES | manual | up | down |
| Vlan1 | unassigned | YES | unset | administratively down | down |
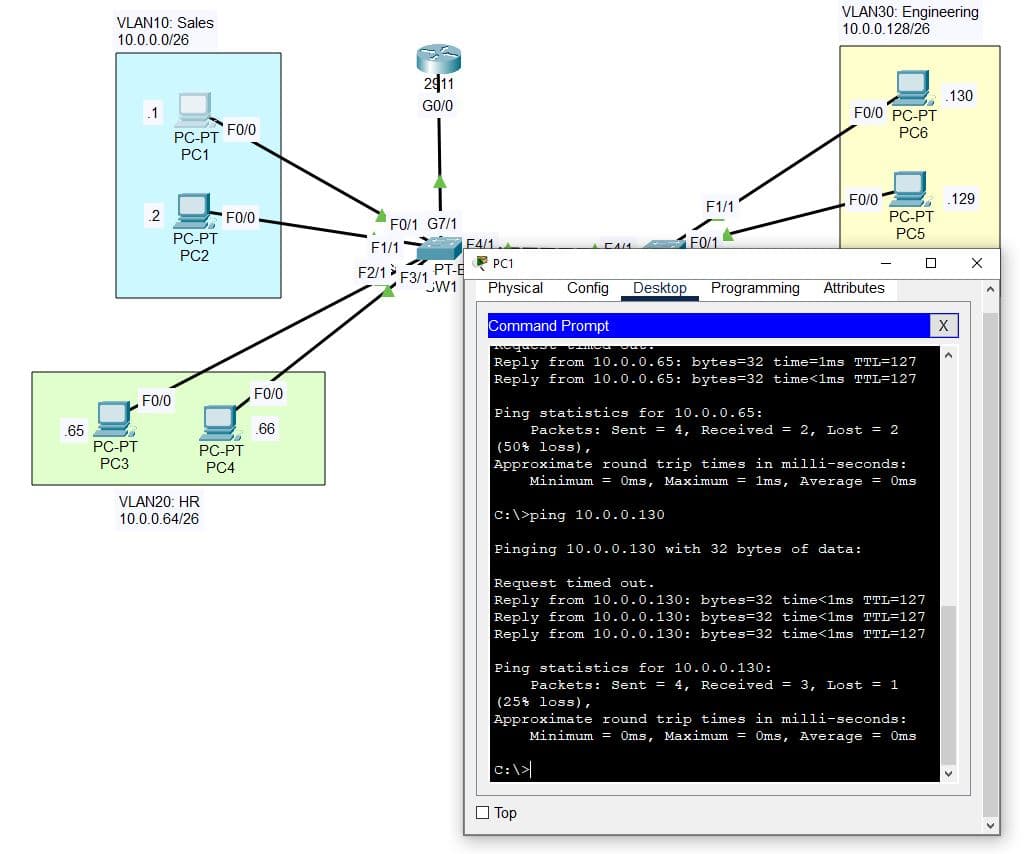
6. Successful Connection
Now testing connectivity by doing a ping test from PC1 to PC5 in a different VLAN and across a trunked switch port, we can see a successful reply letting us know that ROAS has been configured successfully: