Configuring Password Expiration with Group Policy in a Windows Domain
Overview
This lab simulates a domain user's password expiration by configuring the maximum password age via Group Policy in a Windows Server environment. It demonstrates how Active Directory enforces password policies and how clients respond when credentials expire.
| Skills Demonstrated |
|---|
| Configuring Password Policy in Group Policy |
| Managing user accounts in Active Directory |
| Simulating and validating password expiration enforcement |
| Testing domain login behavior on a Windows client |
| Understanding account lifecycle security practices |
| Tools Used |
|---|
| Windows Server (Active Directory Domain Services) |
| Windows 10 Client VM |
| Group Policy Management Console (gpmc.msc) |
| Active Directory Users and Computers (dsa.msc) |
1. Environment Setup
- Installed a Windows Server VM
- Created a local Administrator account
- Installed Active Directory Domain Services (AD DS)
- Promoted the server to a Domain Controller with the domain name:
lab.local

2. User Creation
- In Active Directory Users and Computers, created a domain user:
- Name: John Doe
- Logon Name:
j.doe

3. Configure Password Expiration Policy
- Opened Group Policy Management (
gpmc.msc) - Navigated to:
Default Domain Policy > Computer Configuration > Windows Settings > Security Settings > Account Policies > Password Policy - Set Maximum Password Age to 1 day to trigger a faster expiration

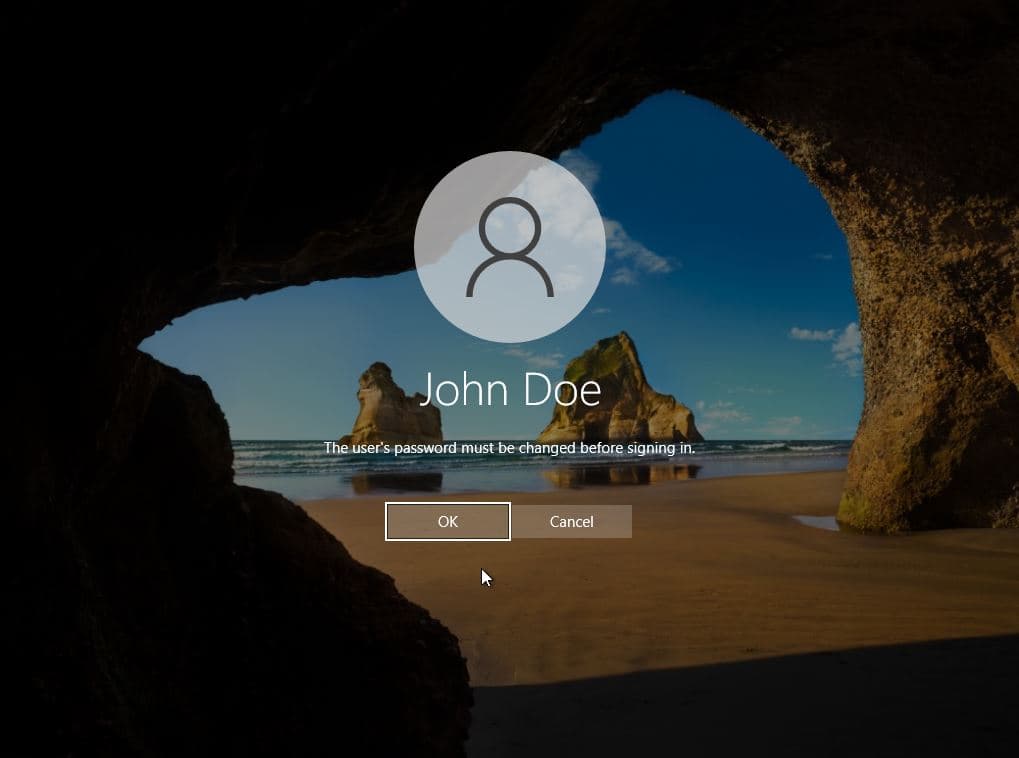
4. Password Expiration in Action
- After one day, logged into the Windows 10 Client VM as
j.doe - Prompted to change the password upon login, indicating successful policy enforcement